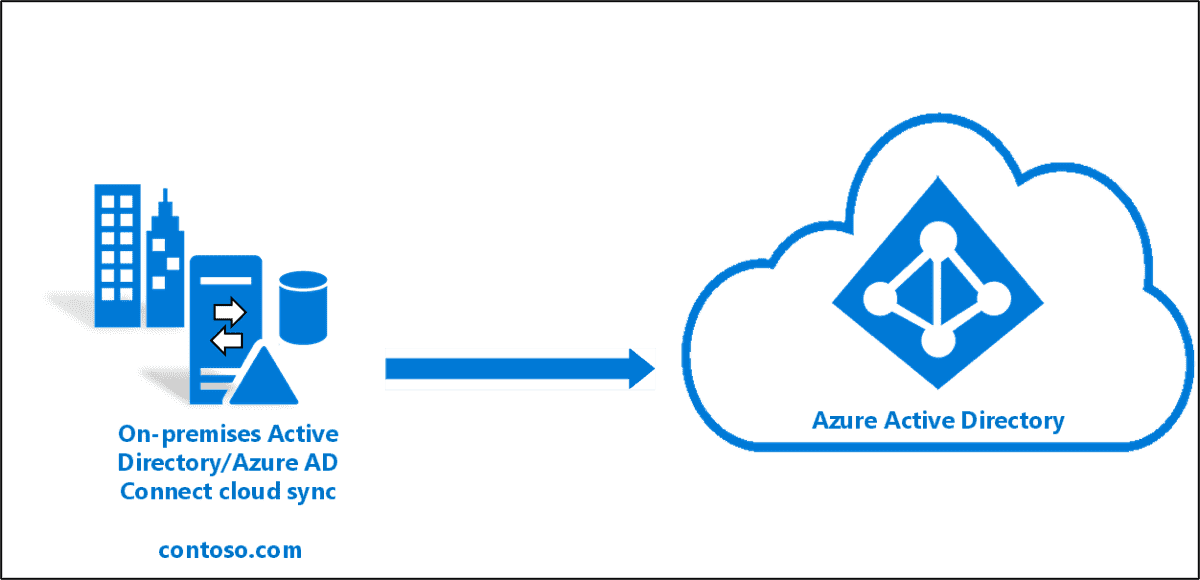
Safeguard your organization against cyber threats and data breaches
- Are you encountering difficulties in ensuring the protection of your organization’s endpoints against cyber threats?
- Do you find it challenging to effectively manage and maintain endpoint security solutions across all devices?

Our Services for Device Endpoint Protection
You have the flexibility to choose the service that aligns with your business requirements:

Risk Assesment
By conducting a comprehensive risk assessment, we identify vulnerabilities within your endpoint security solutions. This allows us to create a tailored security plan that addresses your organization's specific requirements and safeguards against potential threats.

Security Solution Implementation
By utilizing the expertise of our team, we employ advanced endpoint security solutions to safeguard your organization's endpoints against a wide range of cyber threats.
Monitoring and Management
Do you need somebody to manage data security in the company? Do you want to fix any potential endpoint security incidents, minimizing the impact of any security breaches? Additionally, we provide ongoing support to promptly address any user concerns or issues, ensuring a seamless and efficient experience for all.
Security Policy Development
We assist you in creating robust security policies that align seamlessly with your business objectives and adhere to regulatory standards.
Our Frameworks for Collaboration
Fixed Project
Pay a project with a fixed price and have immediate support.
Dedicated Team
Get Part-time or Full-time Engagement models.
On Demand
Pay by the hour with no minimum hour commitment.
What customers say about us
We were in need of assistance for migrating our Dynamics on-premise server to Azure, as well as transitioning our three Active Directory servers to Azure IaaS. We were fortunate to have been assigned consultant Alex, who efficiently handled these tasks with extensive expertise. The process was swift and the consultant demonstrated impressive knowledge. I wholeheartedly recommend engaging with this company.
Oleh
IT ManagerWe required introductory training on M365 products for our workforce of 100 employees. We enlisted the services of Teodor, a fluent German speaker who provided exceptional training sessions to our staff. We highly recommend the IT Partner for their excellent services.
Kai
Company CTOThe company has strong technical expertise in MS Teams and SharePoint, which greatly helped me with PowerShell scripting. They also assisted with migrating our files from Dropbox to OneDrive. In addition, they created an effective strategy for organizing MS Teams channels and successfully implemented Exchange Online. We couldn’t be happier with their trustworthy and efficient services.
Peter
Company CEOI had a remarkable experience working with the engineers from Innovate Digital, who proved to be incredibly helpful and one of the best IT companies I’ve encountered. My objective was to migrate from Dropbox to SharePoint and transition Gsuite accounts to Microsoft. They attentively listened to my requirements and promptly assisted me in achieving my goals. Their expertise in Microsoft products is impressive, and they also maintain a friendly and approachable demeanor. Rest assured, you can trust them completely. I wholeheartedly recommend their services!
Rob
OwnerI had an absolutely fantastic experience collaborating with Radu, an exceptional professional. Our requirement was to find a consultant for HP Enterprise who could assist us in constructing a graph API interface with Intune integration. Radu proved to be a highly skilled System Administrator, and working with him was an absolute pleasure. His expertise in the field was remarkable. Without a doubt, we will be engaging his services and working with his company again in the future.
Matt
IT Department LeadInnovate Digital is the perfect partner for all your MS365 needs. If you’re searching for an expert in MS365 to provide long-term assistance to your IT department, look no further. Their team possesses extensive knowledge and expertise in setting up and maintaining all MS365-related tasks. Additionally, if you’re considering transitioning to the cloud, Innovate Digital is a top recommendation. Their highly skilled professionals have gained invaluable experience working at Microsoft. Don’t overlook the opportunity to collaborate with them for a seamless MS365 experience.
Jorg
Company CEOFrequently Asked Questions
Device endpoint security refers to the protection and security measures implemented on individual devices, such as laptops, desktops, smartphones, and tablets, to safeguard them against various threats and vulnerabilities. It involves deploying security solutions and practices that aim to prevent unauthorized access, data breaches, malware infections, and other cyber threats targeting the endpoints. These security measures can include antivirus software, firewalls, encryption, access controls, patch management, and other defensive strategies to ensure the integrity, confidentiality, and availability of data and resources on the devices.
Endpoint security services offer organizations the following benefits:
- Enhanced protection against cyber threats
- Simplified management of devices and security policies
- Compliance with regulatory requirements and data privacy
- Improved productivity and remote work enablement
- Cost-effectiveness through risk mitigation.
Microsoft Defender Antivirus: A built-in antivirus solution available for Windows devices, providing real-time protection against malware and other threats.
Microsoft Defender for Endpoint: A comprehensive endpoint protection platform that combines threat protection, vulnerability management, and endpoint detection and response (EDR) capabilities to safeguard devices against advanced threats.
Microsoft Intune: A cloud-based endpoint management solution that enables organizations to manage and secure a wide range of devices, enforce security policies, and distribute apps and updates.
Microsoft Azure Sentinel: A cloud-native security information and event management (SIEM) solution that offers intelligent security analytics and threat detection across endpoints and other IT infrastructure.
Microsoft Cloud App Security: A service that helps organizations gain visibility and control over cloud applications and data, providing advanced threat protection and compliance capabilities.
Microsoft Defender for Identity: Formerly known as Azure Advanced Threat Protection (ATP), it is designed to identify and investigate advanced identity-based attacks across on-premises and cloud environments.
Endpoint security services can effectively protect against a wide range of cyber threats, including malware, ransomware, phishing attacks, data breaches, unauthorized access attempts, and other malicious activities targeting endpoints.
The time it takes to adopt endpoint security measures can vary depending on several factors, including the size of the organization, the complexity of the IT environment, and the specific security measures being implemented.
Adopting endpoint security measures typically involves several steps, such as conducting a security assessment, defining security policies, selecting and deploying appropriate security solutions, configuring and testing the systems, and training employees on security practices.
The duration of this process can range from a few weeks to several months, depending on the scope of the implementation and the readiness of the organization. It is important to allocate sufficient time for planning, implementation, and testing to ensure a smooth transition and effective adoption of endpoint security measures.
The cost of endpoint security services can vary depending on several factors, such as the size of the organization, the number of endpoints to be protected, the level of security features required, and the specific vendor or service provider chosen.
Latest Microsoft News
Some interesting ideas and insights you can get from our articles